Bearse Feature ECR Scanner
ECR Scanner periodically scans clusters for images deployed from a central ECR repository for vulnerabilities. Slack notifications are then generated containing a detailed report about the detected vulnerabilities and location of deployed vulnerable images.
Infrastructure
Stacks
- Scanner
- This stack is deployed to the Ops account containing the ECR Repo where the images are stored. It contains the lambda functions responsible for initiating and reporting on image scans.
- ScanAccessRole
- This stack is deployed to all accounts with clusters containing deployed images. It contains the role needed for the scanner to retrieve information on deployed images.
Lambda functions
- Scanner
- Triggered on a daily schedule, this function scans each deployment account for image’s deployed from the Ops account ECR in ECS clusters. All unique deployed images are then scanned for vulnerabilities.
- Notifier
- Triggered when an image scan event is detected, this function retrieves information on the vulnerability details and deployment locations of the scanned image and returns it in a slack notification.
Image Scan Workflow
An example of the general workflow of the ECR scanner is described as follows.
- The feature must be deployed with the scanner in the repo account and the scanaccessrole in each account with any cluster deployments we wish to scan.
- The scanner function is triggered on schedule, it compares all images in the ECR repo with those in each deployment account specified via the scanaccessrole we deployed earlier.
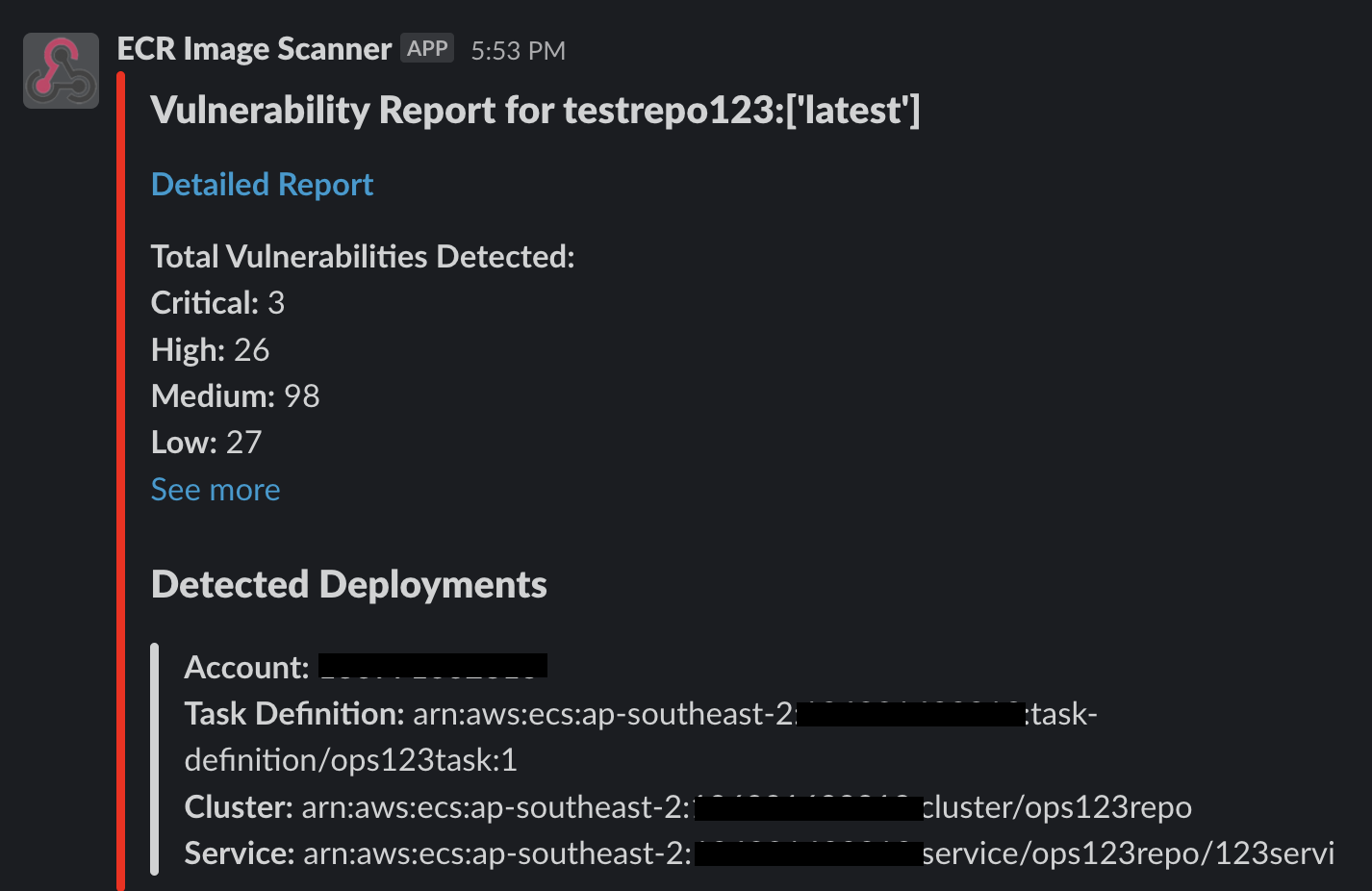
- The notifier function detects the image scan event and generates a report containing the information about detected vulnerabilites and their deployment locations. An example of the report is shown below.
Further information regarding stacks, parameters and deployment details can be found here.